HOW TO BUILD YOUR RESUME
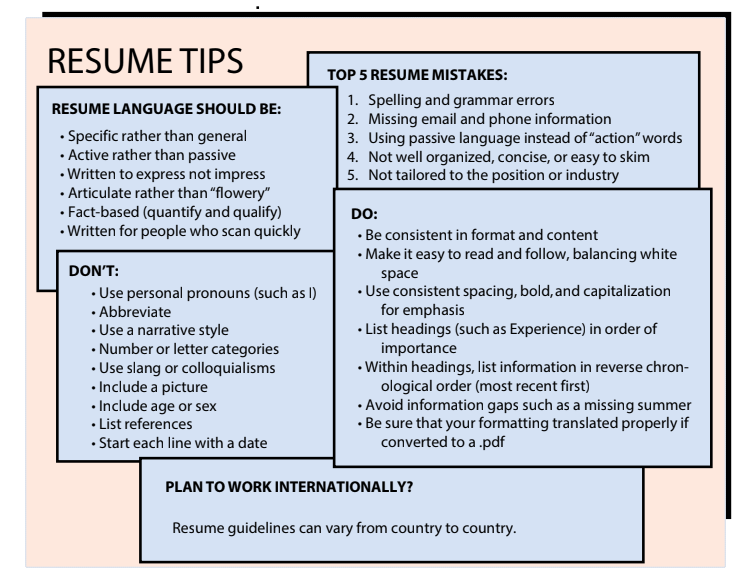
Writing a stand-out resume requires the perfect combination of formatting and content.
Make sure your resume is easy to read, understand, and digest.
I don’t need to say, How CV/Resume and cover letters are important in job searching.
Your resume is a powerful marketing tool to land an interview.
Let’s straight to the point, here I have a collection of highly suggested resume writing tips and CV sample templates from high-standard universities, which allow you to build a powerful CV.
- Create Resume
- Write Cover Letter
- Review for each job before applying
Make use of our CV Samples & Templates and IT Interview Questions

-
Complete Guide to Uptime Kuma: Monitor Your IT Infrastructure with SSL and Microsoft Teams Alerts
Scenario: Why SLA Monitoring Matters You’re managing IT with limited resources. One night, a key service goes down, and you only hear about it the next morning from an angry user. Now you’re chasing logs, explaining delays, and scrambling to meet audit requirements. What if you had a simple monitor that alerted you the moment…
-
Nmap Network Scanning: A Hands-On Cybersecurity Lab (2025 Edition)
Nmap (Network Mapper) is a must-have tool for anyone interested in cybersecurity, ethical hacking, or network administration. It helps you scan networks, find active devices, detect open ports, and gather information about running services. For beginners, Nmap is a great way to understand how networks work and how attackers find security weaknesses. For intermediate students,…
